Could you imagine what it would be like if your every move were being tracked? If your every word was being monitored by someone with a nefarious purpose?
Well, as consumer-grade surveillance technology continues to evolve, it’s becoming more and more possible that your entire life could be compromised. Even more terrifying, the person responsible could be someone close to you. There was recently a horrifying story that puts a spotlight to this stomach-churning possibility.
The Unthinkable
Mark Gerardot and Jennair Gerardot were married for 24 years. After a period of separation due to work, they were reunited in Delaware, but something had changed. Jennair soon suspected that Mark had been having an affair with Meredith Chapman, a woman he had met from his work at the University of Delaware. Mark denied these suspicions, so Jennair serendipitously stole his phone, taking it to a security company to be unlocked. With her fears confirmed by texts and Snapchat messages, Jennair confronted Mark, who soon admitted to everything.
From a security perspective, this is already horrific, but it gets much worse. After the affair was uncovered, the couple went to counseling, eventually separating and starting to go through a divorce.
While it appeared that Jennair was moving on with her life, the reality was that she was planning her revenge. A few months after the separation, without warning or suspicion, Jennair killed Meredith Chapman and then herself in a murder/suicide.
With his life in ruins, it wasn’t until later that Mark started to look into the comprehensive surveillance campaign that his ex-wife launched against him after their separation. It turns out that every aspect of his life, and much of Meredith’s, has been entirely compromised by Jennair using nothing but commercially-available equipment.
Her Equipment
Long-lasting recording devices are readily available online, and Jennair made use of them. She had sewn recording bugs into Mark’s jackets and clothes, recording his every word, and everything said around him. His office and other private spaces were also bugged. Jennair transcribed every word of these recordings into 12 total notebooks between the separation and murder.
Jennair also purchased a lockpicking kit to break into Mark’s office, hacking software to break into his computer, DNA testing for his clothes, and a GPS system that she installed in both his and Chapman’s cars. This allowed her to track almost their every move.
In some cases, she didn’t even need to use commercially-available technology to get access to Mark’s entire life. Allegedly, she unlocked his phone using his thumbprint when he was sleeping, giving her access to his text messages and SnapChat, without having to go to a security professional to break in.
Finally, she had also purchased a firearm, five weeks prior to using it.
Everything was bought with credit cards, no security or waiting period required. Once Jennair had these surveillance resources at her disposal, there was no stopping her. Everything was done in secret, with Mark and Meredith having no idea that they were being recorded or tracked.
The Danger
While this situation is unique and thankfully rare, it only goes to show how easy it is to compromise every aspect of another person’s life with readily-available equipment off the shelves. People don’t need cutting-edge espionage tools to run a remarkably professional surveillance campaign against you.
With these few simple and relatively cheap resources, Jennair Gerardot managed to track two people accurately, record days’ worth of conversations, break into their offices, and much more. She didn’t even need specialized help to get into his phone for access. All she needed was his thumb.
Smart people know to target the weak points in someone’s life. If you’re an executive at a major organization, people who wish to dig up dirt on you or steal proprietary information know how difficult it’s going to be to bug your work office. But breaking into your home, bypassing your security system, hacking into your home computer, and planting bugs? That’s comparatively easy.
The potential danger is clear for any executive, high-net-worth individual, or spouse. If you wish to keep your private life private, you need to take steps to ensure that you have not been compromised.
The Solution
On occasions like this, there can be few to no warning signs that someone else has complete access to your life, home, and office. Unless you get lucky by discovering a bug accidentally, you can be tracked and recorded without any signs of surveillance. This is why utilizing Residential TSCM Services is essential to confirm your private life is, in fact, private.
When we visit your home, we will check your computers and smartphones for spyware and malware. If any is found, we will tell you when and how it was installed. We also check your vehicle to make sure that it isn’t being tracked with GPS. We will inspect your home for traditional and cyber eavesdropping devices, including ones that utilize bluetooth, wifi, or cellular networks. At the end of the assessment, you will receive a PDF report detailed the services performed, our findings, and our recommendations to help you protect your privacy moving forward.
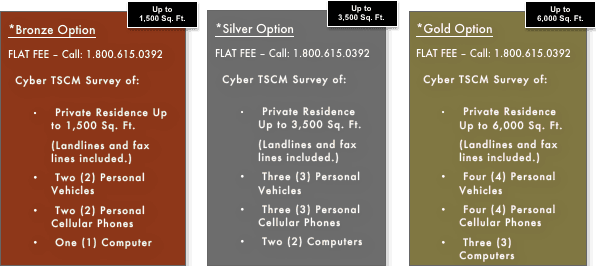
With our Residential TSCM Services, we offer packages that will detect electronic eavesdropping and help you regain your privacy and peace of mind:
If you’d like to learn more about our Residential TSCM Services, you can read more here. Our Home Bug Sweeps detect illegal surveillance and restore your privacy at home. And chances are that if you’re an executive or business owner and your private life has been compromised, then your work life may have been as well. Our Corporate TSCM Services detect illegal surveillance and restore privacy at the office. If you have any questions about our TSCM/Cyber TSCM Services and how to best protect your privacy at home and at work, please feel free to contact us today!
About the Author:
 J.D. LeaSure, CCISM, is the President / CEO of ComSec LLC, a global provider of world class counterespionage and TSCM / Cyber TSCM™ services. www.ComSecLLc.com
J.D. LeaSure, CCISM, is the President / CEO of ComSec LLC, a global provider of world class counterespionage and TSCM / Cyber TSCM™ services. www.ComSecLLc.com