Counter Surveillance Services
Do You Need Counter Surveillance Services? Call ComSec LLC at 1-800-615-0392 !
Professional Counter Surveillance Services
Concerned your business or home is under technical surveillance? You Can Trust Your Counter Surveillance Service Needs to ComSec’s Team!
ComSec LLC is a leading provider of professional counter surveillance services in the USA and globally. We serve government, military, businesses, non-profits, executives, high risk individuals and residential clients. Our skilled counter surveillance specialists use advanced TSCM equipment to detect the full range of technical surveillance devices and threats. In fact, our expertise and equipment set us apart from other providers.
ComSec LLC’s counter surveillance services include both TSCM and Cyber TSCM. We detect bugging devices that use a network such as bluetooth, wi-fi or cellular to send the collected information to the spy. And, we also address vulnerabilities with bluetooth, wi-fi and cellular networks that can be exploited for technical surveillance purposes. So, our counter surveillance services address the advanced technical surveillance threats and vulnerabilities of our “connected” world.
Equally important, our services also detect less advanced bugging devices that require recovery of the bugging device to access the collected information. These older technology devices are often used when a spy suspects strong cyber defenses that will be difficult to defeat. All in all, ComSec LLC’s counter surveillance services are a comprehensive and effective solution.
Read client testimonials to learn more about the level of service excellence we provide.
Complete a Secure Contact Form or Call ComSec LLC Today 1-800-615-0392 For More Information!
Learn More About ComSec LLC’s Services
Corporate Counter Surveillance Services

View our Corporate Brochure
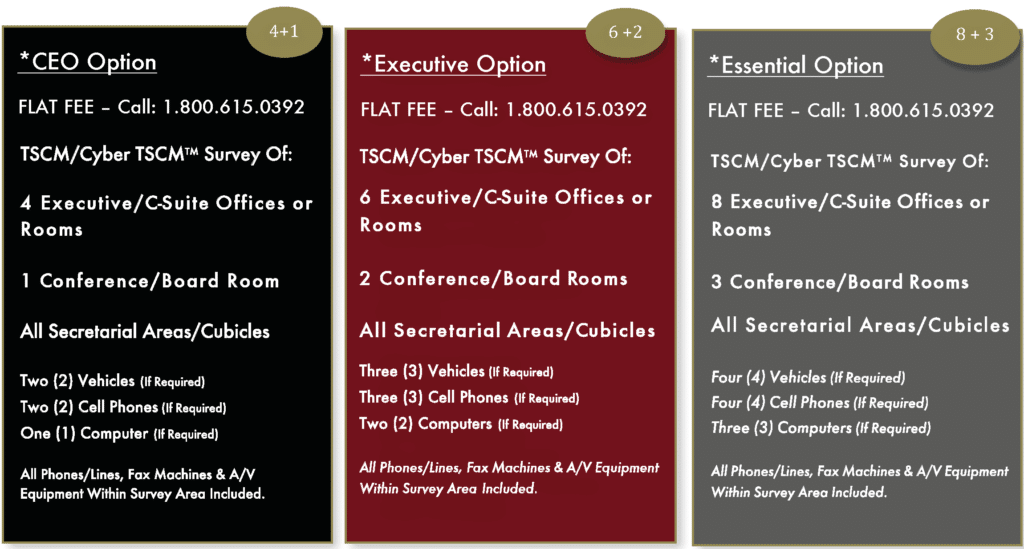
ComSec LLC’s Corporate Counter Surveillance Services include:
- Technical threat assessment
- Full physical and electronic TSCM / Cyber TSCM survey
- Illicit IMSI Catcher Detection
- Phone closet, phone lines and instruments (if requested)
- Wi-Fi security examination
- Network room(s) (if requested)
- Locating bugging devices
- Identifying technical security vulnerabilities
- Verbal debrief on site
- Electronic survey report within five (5) business days of completing services
- Recommendations to improve your technical security posture
- Spyware/malware detection for mobile devices and computers (if requested)
- GPS tracker and electronic eavesdropping device detection for vehicles (if requested)
Our business clients include Fortune 500 corporations to small businesses. We serve clients in government, defense, critical infrastructure, legal, technology, news media, non-profits, and many others industry sectors.
We offer surveys for 200,000+ sq. ft. facilities to C-Suite office wings. Packages are customized based on survey area size, and the scope of the assignment. Or, choose one of our all inclusive options:
Our Counter Surveillance Services can be provided overtly or covertly. Evening or weekend appointments are available for your convenience at no additional charge. Inspections can typically be performed at your location within 48 hours of receiving your completed Service Quote.
Complete a Secure Contact Form or Call ComSec LLC Today 1-800-615-0392 For More Information!
Residential Services

View our Residential Brochure
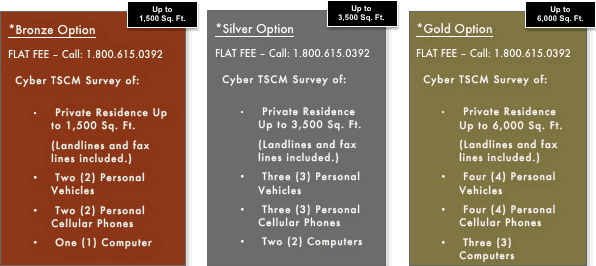
To summarize, ComSec LLC’s Residential Counter Surveillance Services include:
- Technical threat assessment
- Full physical and electronic TSCM / Cyber TSCM survey
- Illicit IMSI Catcher Detection
- Wi-Fi security and Wi-Fi environment examination
- Spyware/malware detection for mobile devices and computers
- GPS tracker and electronic eavesdropping device detection for vehicles
- Locating electronic eavesdropping devices
- Identifying vulnerabilities
- Verbal debrief on site
- Electronic survey report within five (5) business days of completing the survey
- Recommendations to improve your technical security posture
ComSec LLC provides residential counter surveillance services for homes of all sizes, from estates to executive apartments. We serve high net worth individuals, celebrities, politicians, dignitaries, high profile targets and executives. We offer surveys for 30,000+ sq. ft. estates to executive apartments.
Home services can be provided overtly or covertly. Evening or weekend appointments are available for your convenience at no additional charge. And, we can typically provide counter surveillance services within 48 hours of receiving your completed Quote.
Packages can be customized based on the size of the survey area, and the scope of services. Or, choose one of our all inclusive options:
Complete a Secure Contact Form or Call ComSec LLC Today 1-800-615-0392 For More Information!