Choose IMSI Catcher Surveillance Detection Services As:
- A standalone service;
- Included with In-Conference Monitoring Services
- As a business TSCM service package; and
- During contracted Assurance Option Services.
IMSI Catcher Detector Services
The Extent of the Threat
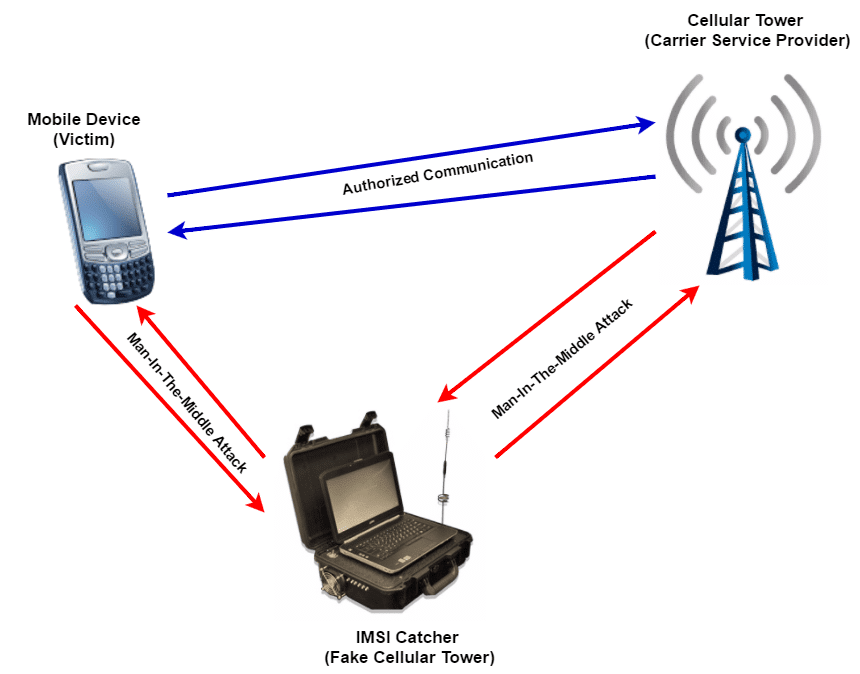
Federal law enforcement agencies, as well as state and local agencies, use stingray devices and other forms of IMSI catcher technology as an investigative tool. But, this technology is also available to foreign governments and foreign intelligence services, authoritarian regimes, via the black market in China, hackers, etc. If your business information or customer information is of value to an entity with access to the IMSI catcher technology, you have cause for concern. ComSec’s IMSI Catcher detection services are a strategically important tool for any business that may be targeted for cellular surveillance.
How Compromised Cellular Devices Can Be Used
- To conduct nation state sponsored industrial or economic espionage attacks.
- To manipulate or control domestic or foreign affairs that affect policy or regulatory issues.
- To capture sensitive or privileged communications and outmaneuver an adversary.
- To steal development, engineering or other valuable intellectual property information.
- To identify clients, suppliers or other contacts.
- To capture damaging personal information about a business, its leadership or owner(s).
- To interrupt or stop important business communications.
IMSI Catcher Detector Features
- Can identify illegal IMSI catchers, cellular jamming, rogue base stations and baseband attacks.
- Provides comprehensive air interface data analysis and geo referencing.
- Mobile system architecture for on-site detection capabilities.
- Carrier grade SLA, CARE, incidents.
- Compatible with operator redundancy and/or visualization requirements.
- Reports provide intelligence at a city level, street view . . all the way down to cell details, cell comparisons and critical criteria editing.
How A Stingray Device Works
Active Mode:
- Extracts stored data (e.g. International Mobile Subscriber Identity (“IMSI”) numbers and Electronic Serial Number (“ESN”) and uses this information to identify the target;
- Writes cellular protocol metadata to the cellular device’s internal storage to control its behavior;
- Forces signal transmission power to increase so it can overtake the cellular device(s);
- Forces a significant quantity of radio signals to be transmitted;
- Intercepts communications content by tricking the cellular device into believe the stingray is a legitimate cell tower;
- Allows tracking and locating the cellular device user even while the device is not being used for a call or to access data services;
- Conducts a denial of service (DOS) attack so service to the cellular device is interrupted;
- Extracts encryption key(s) so it can trick the cellular device into recognizing the roque cell tower as a legitimate cell tower; and
- Radio jamming for either general denial of service purposes or to aid in active mode protocol rollback attacks.
Passive Mode:
- Conducts base station surveys to identify and map the coverage areas of legitimate cell towers.
