Technical Surveillance Countermeasures
Technical Surveillance Countermeasures is a present and increasing necessity. The number of electronic devices that connect with networks, and with other connected devic
In 2024, there were about 18 billion active IoT-connected devices globally, according to Statista. And, this number is forecast to grow to more than 32 billion by 2030. As the connectedness of our world increases, so does the risk of technical surveillance, and even more so the need for technical surveillance countermeasures.
The Purpose of Technical Surveillance Countermeasures
Technical surveillance countermeasures addresses unauthorized technical access to proprietary, trade secret, controlled or private information. This access may occur in a government facility, data center, financial institution, law office, corporate C-suite, rented conference room, aircraft, or a private home. The exposed information may cause a loss of revenue, theft of proprietary information, exposure of customer data, loss of personal privacy, threats to safety, etc.
While technical surveillance countermeasures was once thought of as international spy craft, in the modern connected world, it touches each of our lives in one form or another. We have all been impacted by exposures, whether directly or indirectly. Some examples are networks exfiltrating data, database leaks, AI orchestrated hacking, smart device vulnerabilities, GPS tracking of vehicles, hidden cameras, spy gadgets disguised as common items, spyware on mobile devices, etc. And, connections to insecure or compromised networks multiply the dangers for the connected devices, and ultimately the users. In our connected world, we are all at risk and in need of technical surveillance countermeasures to stop information theft and protect privacy.
Often TSCM is performed in reaction to a perceived threat. However, technical surveillance countermeasures is best performed as a pro-active strategy to reduce the risk of exposure, and to avert the ramifications of those exposures. Ultimately, in high risk environments, proactive TSCM sweeps are performed on a routine basis in conjunction with in place monitoring. However, in-place monitoring alone is never a suitable substitute for full scope technical surveillance countermeasures examination.
How Is Technical Surveillance Countermeasures Performed
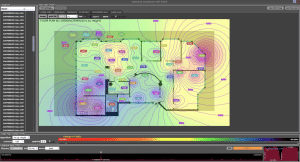
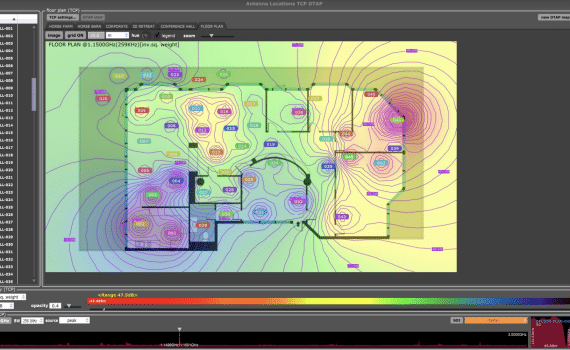
Technical Surveillance Countermeasures is focused on detecting, identifying and locating bugging devices and technical security exposures in a survey area(s). It is a methodical and in-depth process conducted by a skilled, experienced practitioner using specialized TSCM equipment. Physical, electronic and network inspections are integral aspects of comprehensive TSCM services. Mobile devices and vehicles should also be examined to ensure all threat vectors are addressed.
Inspections & Examinations
Physical Examination:
It’s a visual inspection to locate bugging devices, physical security issues, and evidence of tampering. Examples are tampering include dust, moved ceiling tiles, newly patched or painted surfaces, damaged or modified walls, misaligned electrical outlets, additional cables or cabling, etc. Essentially, the TSCM practitioner visually scans the survey area, and may use tools and equipment, for overt intel about the current state and what has transpired in the survey area prior to their arrival. Physical vulnerabilities like faulty locks, poorly places sensors, passwords in easy to find places, among others, are also noted and brought to the attention of stakeholders.
Electronic Examination:
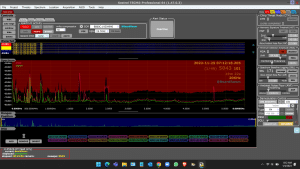
During the electronic TSCM inspection specialized equipment scans the survey area(s) for detect of electronic surveillance bugs and technical security vulnerabilities, and provides action 
Technical surveillance countermeasures must detect active, passive and switched off devices. This ensures bugs that may not be operating during the TSCM inspection, such as store and forward bugs, are also detected.
And, spyware/malware programs on mobile devices that can record keystrokes or use the camera or microphone just as they would a bug, are ncessary. This examination is conducted on cell phones, tablets, laptops and desktop computers. And, GPS trackers, electronic eavesdropping threats and personal electronics (e.g. AirTags, AirPods, etc.) in/on vehicles is also important.
Network Examination:
The network technical surveillance countermeasures inspection addresses:
- Wi-Fi: Security, segmentation, credentials, access points, authorized and unauthorized connected devices, and network behaviors.
- Bluetooth: Devices in the survey area, those paired to mobile devices, personal electronics that are not designed or intended for surreptitious purposes, such as AirPods and AirTags that can used for surreptitious purposes.
- Cellular: Cellular repeaters, cellular phones in the survey area, identification of illicit cellular BTS, etc.
- Other networks that may be transmitting in the service area(s), such as Zigbee, SigFox, etc.
TSCM Equipment
Specialized technical surveillance countermeasures equipment is necessary to effectively perform professional TSCM services. The equipment must be capable of detecting, identifying and analyzing signals emitted by technical surveillance devices within the survey area. And, Cyber TSCM equipment must be used to detect networks, access points and the associated electronic devices that may compromise privacy. As well, capabilities must include detection of active, passive and switched off electronic devices. Direction finding and signal strength capabilities are also needed so surreptitious signals can be investigated and the threats located.
Frequently used technical surveillance countermeasures equipment includes:
-
- RF spectrum analyzers
- Hidden camera detectors
- Optical threat detectors
- Wired device detectors
- Wireless device detectors
- Thermal imagers
- Telephone line and instrument analyzers
- Wi-Fi analyzers, Bluetooth and cellular network analyzers
- Cellular tower detectors
- Non linear junction detectors,
- Magnetometers, etc.
TSCM equipment must cover a full range of technical surveillance threats. The radio frequency range, accuracy, precision and actionable intelligence provided by the equipment is critical to the success of the inspection.
As well, providing Clients with actionable intelligence about issues with surreptitious networks, access points and Cyber TSCM bugs in the survey area is required, so appropriate countermeasures can be implemented.
REQUEST QUOTE
About ComSec LLC
ComSec LLC is a leading Technical Surveillance Countermeasures company in the USA, and globally. We serve government, military, corporations, non-profits, dignitaries, celebrities, executives, HNWIs, and other high risk individuals. Our proprietary detection methodologies, skilled TSCM Specialists and advanced detection equipment set us apart from other providers. And, we update our methodologies and equipment to ensure we are able to detect electronic eavesdropping devices and threats from the low tech, inexpensive to the most advanced.
Above all, we are well known for our electronic eavesdropping detection capability, our countermeasure recommendations and our aim of restoring your privacy.
Learn More: