TSCM
What is TSCM

Technical surveillance countermeasures also includes Cyber TSCM. Cyber TSCM detects electronic surveillance via networks, network connected devices and vulnerabilities in these networks (e.g. wi-fi, BlueTooth, cellular, etc.) And, yet another aspect of TSCM is detection of hybrid technical surveillance devices.
TSCM is a counter intelligence discipline. It addresses technical surveillance as an ever evolving threat landscape. And, it requires continual examination of emerging threats, developing the needed detection capabilities and implementing appropriate countermeasures. TSCM is not static, but dynamic and continually changing.
Risk reduction strategies include TSCM as a means of reducing theft or loss due to nation state sponsored, critical infrastructure, economic espionage, industrial espionage and/or insider threat based electronic eavesdropping attacks. Risks to critical infrastructure, protected information, intellectual property, trade secret, proprietary information and competition sensitive information must be addressed. And, TSCM, when complimented by Cyber TSCM, addresses a full range of technical surveillance threats needed for an effective risk reduction strategy.
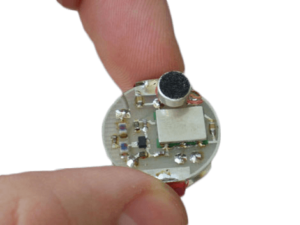
Bugging Devices
Bugging devices include those that were specifically designed and intended for capturing information by surreptitious means. These include audio and video bugs that do, or do not, connect to a network. Examples include: hard wired eavesdropping bugs, battery operated bugs, hidden cameras, store forward burst devices, audio recorders, etc. As well, bugging devices also include items that were designed for surreptitious purposes, but can be used for surreptitious purposes (e.g. AirTags, AirPods). A skilled TSCM practitioner can detect a full range of technical surveillance threats.
What is Technical Surveillance
Technical surveillance is accomplished by using bugging devices, networks, technologies and/or exploits to collect information from a target(s) in an unauthorized manner. Typically, the information captured is in audio and/or video format. Information targeted for technical surveillance collection typically has monetary value, national or strategic value, may provide leverage, and/or cause harm.
TSCM Sweep

The TSCM physical inspection identifies physical damage, signs of tampering, the visual presence of covert devices and other visual clues of technical surveillance.
The electronic inspection is performed with a variety of signal analysis equipment that detects the frequency of active or transmitting devices and threats. Devices that are in a passive state (turned off, in standby mode, etc.) are also detected with equipment that causes passive devices to become active or equipment that can detect electronic components, such as an NLJD.
The network inspection includes WiFi, Bluetooth and cellular networks, IoT devices, illicit IMSI catchers, etc. Personal electronics that were not meant for surreptitious purposes, such as AirPods and AirTags, but which can used for surreptitious purposes, are also included in the network inspection.
REQUEST QUOTE
What Are Countermeasures
Countermeasures are devices, technologies or strategies that are put in place to preclude the success of technical surveillance attacks. Often, needed countermeasures are identified during a TSCM inspection. As well, identification of countermeasures can result from identification of known risks such as industry specific, geographical, or other dynamic known to introduce or elevate certain risks.
About ComSec LLC
We are a leading provider of TSCM Services in the USA, and globally. Our customers include government, military, corporations, non-profits, dignitaries, celebrities, executives, HNWIs, and other high risk individuals. We serve Fortune 100 businesses to small businesses. And, our residential clients include business owners, executives and others who believe their privacy has been compromised.
ComSec LLC uses proprietary detection methodologies, skilled TSCM Specialists and a variety of advanced detection equipment. We also update our methodologies and technical equipment to ensure we are able to detect electronic eavesdropping devices and threats from the low tech, inexpensive to the most advanced. Above all, ComSec is renowned for our electronic eavesdropping device detection capability and our goal of restoring privacy.